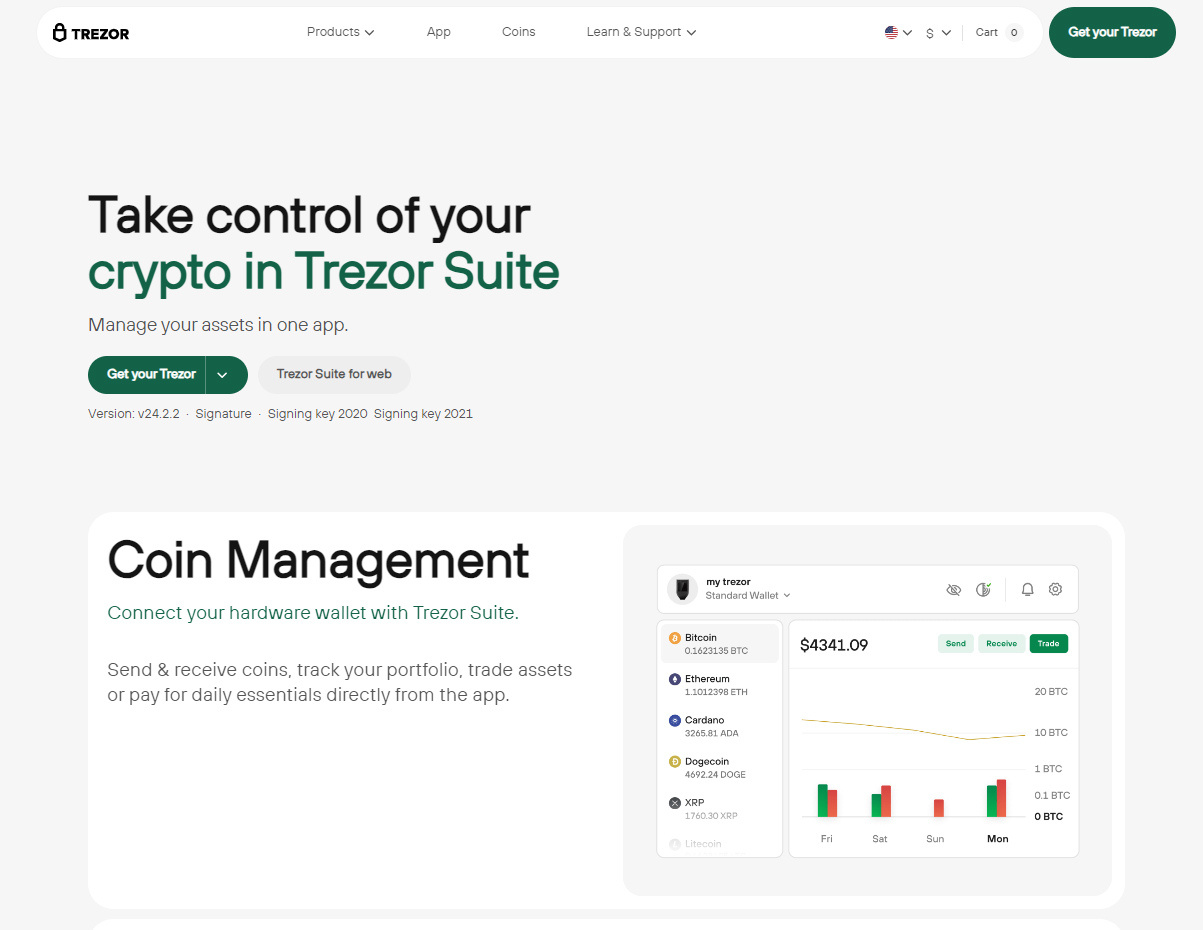
Trezor Bridge | Introducing The New Trezor App
How to Install Trezor Bridge
Step 1: Download the Software
To begin, visit the official Trezor website and navigate to the Trezor Bridge download page. Ensure you download the software compatible with your operating system, whether it be Windows, macOS, or Linux.
Step 2: Install Trezor Bridge
Once downloaded, open the installation file and follow the on-screen instructions to install Trezor Bridge on your computer. The process is straightforward and typically takes only a few minutes.
Step 3: Connect Your Trezor Device
After installing Trezor Bridge, connect your Trezor hardware wallet to your computer using a USB cable. Ensure that your device is properly connected and powered on.
Step 4: Access Trezor Wallet
Open your web browser and navigate to the Trezor Wallet interface. Trezor Bridge will automatically detect your hardware wallet, allowing you to manage your cryptocurrency assets securely.
Benefits of Using Trezor Bridge
Increased Usability
Trezor Bridge simplifies the process of managing your cryptocurrency assets by eliminating the need for browser extensions. This increases usability and ensures a more intuitive experience for both novice and experienced users.
Superior Compatibility
By supporting major web browsers, Trezor Bridge ensures that users can access their Trezor Wallet from virtually any device with an internet connection. This broad compatibility enhances the flexibility and convenience of managing your digital assets.
Robust Security
Trezor Bridge enhances the security of your cryptocurrency transactions by providing an encrypted communication channel between your hardware wallet and the Trezor Wallet interface. This ensures that your private keys remain secure and inaccessible to potential online threats.
Automatic Maintenance
The automatic updating feature of Trezor Bridge ensures that your wallet remains protected against the latest security threats. This reduces the burden of manual updates and ensures that you are always using the most secure version of the software.